In case most of you didn’t know, Azure Active Directory (AD) Premium service reached general availability in April 2014. Azure AD Premium is an identity and access management service that resides on the Azure platform.
For those of you not familiar with Microsoft Azure Active Directory, it provides an easy single sign-on experience to over 1,100 cloud services including Box, Concur, Salesforce.com, and Microsoft cloud services such as Office 365, Windows Intune, and Dynamics CRM—on nearly every device and many browsers. With Azure AD Premium you can reset forgotten passwords, manage their groups, and set up your own company branded portal(s) for launching these software as service (SaaS) applications with a single set of corporate credentials. IT can continue to protect data on any cloud with synchronization to on-premises Active Directory, machine based learning security reports, alerting, and even multi-factor authentication. Azure AD provides a rich standards-based platform that enables developers to deliver authentication and access control to their applications, based on centralized policy and rules. Let’s give IT some control back!
So what’s the difference between Azure Active Directory and Azure Active Directory Premium?
Well, first the features:
– Application access management: Azure AD Premium lets you assign application access to users using groups, which enables you to efficiently manage the end-to-end process for application access.
– Self-service password reset: The self-service password reset feature enables your organization to reset their passwords without calling your help desk. It now lets you use Azure AD Premium to reset on-premises passwords in Windows Server Active Directory.
– Self-service group management: The self-service group management feature gives you the ability to delegate group management to your users. With this feature they can create groups and manage memberships in groups they own.
– Multi-Factor Authentication: The multi-factor authentication feature enables you to quickly and easily set up a multi-factor authentication solution for your organization without deploying new software in your local network or distributing hardware to your employees.
– Customized branding: AD Premium enables you to brand the sign-in experience that end users see when they sign on to applications. Users will see your organization-specific branding across more of their sign-in experiences.
– Reporting, alerting, and analytics: The reporting, alerting, and analytics capabilities give you visibility into potential security concerns and into cloud application usage by users in your organization.
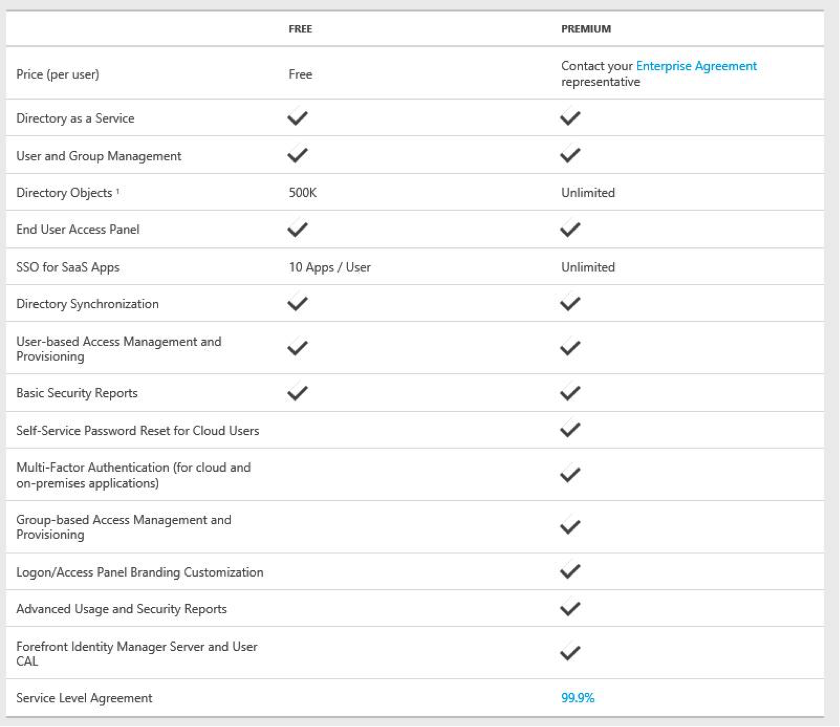
Secondly there’s the pricing:
– Enterprise Agreement: Azure Active Directory can be added on to your existing volume licensing agreement and will have a subsidized cost in relation to total licensing count and Azure services subscribed to—unfortunately Microsoft does not give retail pricing estimates for this service as of yet. However, I have been able to determine it ranges from $4 to $6 per user (no guarantees, as Microsoft controls pricing on these products).
– Enterprise Mobility Suite: Includes Azure AD Premium, Windows Intune, as well as Azure Rights Management. Microsoft offers about a 70% discount on this package; sold separately would be about $12 per user and with the bundle it would be about $8 per user (no guarantees, as Microsoft controls pricing on these products). See more on pricing from Microsoft.
Self-Service Password Reset
Now let’s look at what self-service password reset looks like.
First, some prerequisites to setting this up to allow on-premises AD password reset:
– Active Directory on-premises (2008 R2 or higher)
– Active Directory Federation Services deployed and configured
– Directory Synchronization to Azure Active Directory
– Azure Active Directory Premium Enabled for your organization
We need to set up password reset policy configuration settings:
You can configure the self-service password reset policy for a specific directory using the Azure Management Portal under the user password reset policy section in the directory’s Configure tab. From this configuration page you can control many aspects of how this feature will work in your organization. Here’s how to set it up:
– Open a browser of your choice and go to the Azure Management Portal.
– In the Azure Management Portal, find the Active Directory extension on the navigation bar on the left hand side.
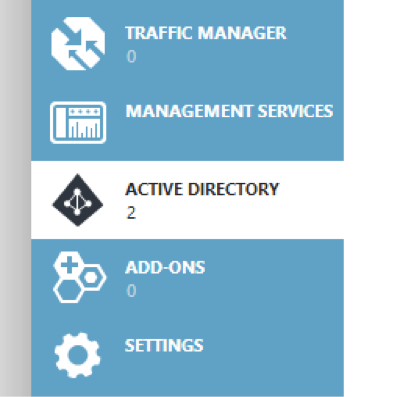
– Under the Directory tab, click the directory in which you want to configure the user password reset policy, for example, Marlin (me).
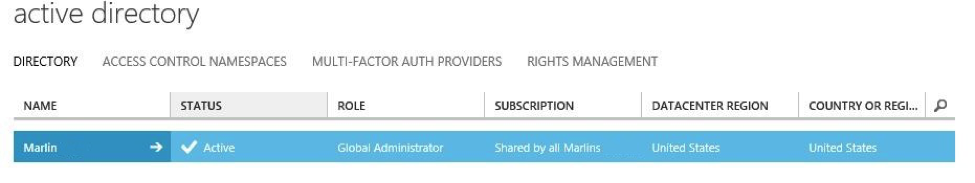
– Click the Configure tab.
Under the Configure tab, scroll down to the user password reset policy section. This is where you configure every aspect of user password reset policy for a given directory. If you don’t see this section, make sure you have signed up for the Azure Active Directory Basic and Premium Editions and that the premium features toggle is set to enabled.
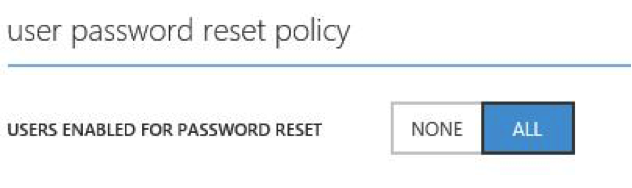
If set to none, no users can register their own challenge data.
If set to all, any user in the directory can register challenge data by going to the registration portal at http://aka.ms/ssprsetup.
If set to all, users are able to reset their passwords automatically by going to http://passwordreset.microsoftonline.com or clicking on the “Can’t access your account” link on any organizational ID sign-in page.
Here’s a list of the options you can set:
Setting the number of challenges (either one or two) a user must go through to reset his or her password.
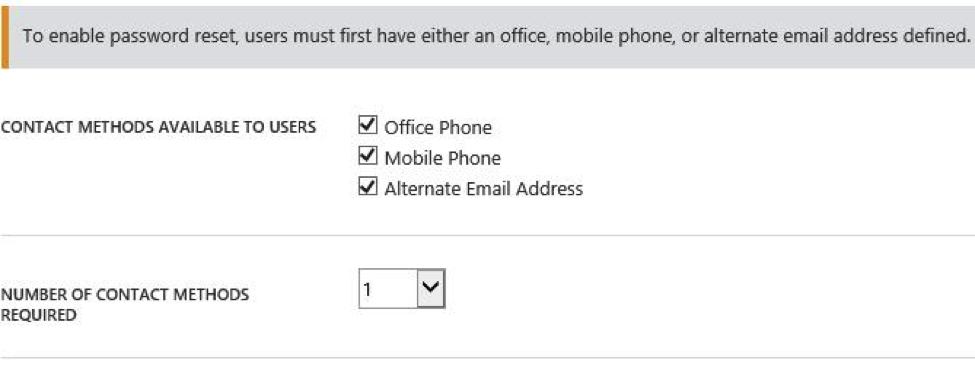
Setting the specific types of challenges you want to enable for users in your organization from the choices below: (NOTE: if this is an on-premises user synced to Azure AD these credentials must be added to their account properties in Windows Active Directory)
Mobile phone (a verification code via text or a voice call)
Office phone (a voice call)
Alternate email (a verification code via email)
Requiring users to register for password reset when they go to the application access panel at http://myapps.microsoft.com.

Requiring users to re-confirm their previously registered data after a configurable number of days have passed.

Providing a help desk email or URL that will be shown to users in case they have a problem resetting their passwords.

Branding the user password reset portal with your organization’s logo and name by using the tenant branding customization feature.
__
__
Setting Up On-Premises AD Password Reset
Now here are just a few side notes to set up on-premises AD password reset.
Password writeback is a Directory Sync Tool component that can be enabled and used by the current subscribers of Azure Active Directory Premium. It allows you to configure your cloud tenant to write passwords back to your on-premises Active Directory. It allows you to avoid having to set up and manage a complicated on-premises self-service password reset solution, and it provides a convenient cloud-based way for your users to reset their on-premises passwords wherever they are. The process to enable this is located here. We set this up for the rest of the blog to allow us to reset our on-premises AD passwords; I followed these very instructions. (NOTE: This feature is in public preview. You may use it in your production environment, but note that you will need to upgrade to a new version once the feature is generally available. This feature will not be officially supported by Microsoft until it reaches general availability.)
Before users are able to use password reset, their user accounts (cloud or on-premises) must be updated with the correct contact data to ensure they can pass through the appropriate number of password reset challenges defined by an administrator. Today an administrator can set this up either through the Azure or Office web portals, through DirSync, or through Windows PowerShell.
However, if you’d rather have your users register their own data, Microsoft also provides a web page that users can go to in order to provide this information. Currently, this page requires that users provide and verify their mobile phone numbers and alternate email addresses. Once this data is verified, it is stored in their cloud user account to be used for account recovery at a later time.
Resetting Your Password
Now that you’ve configured a user reset policy and specified contact details for your users, users can perform a self-service password reset.
To perform a self-service password reset:
1. If you go to a site like portal.microsoftonline.com, you’ll see a login screen like the one below. Click the “Can’t access your account” link to test the password reset function.
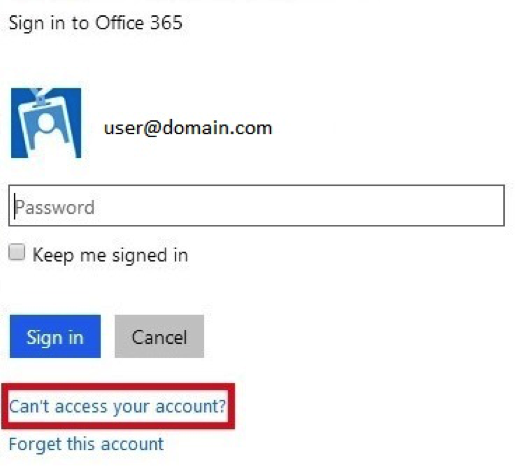
2. After clicking “Can’t access your account”, you are brought to a new page which will ask for a user ID for which you wish to reset a password. Enter your test user ID here, pass the captcha, and click “Next”.
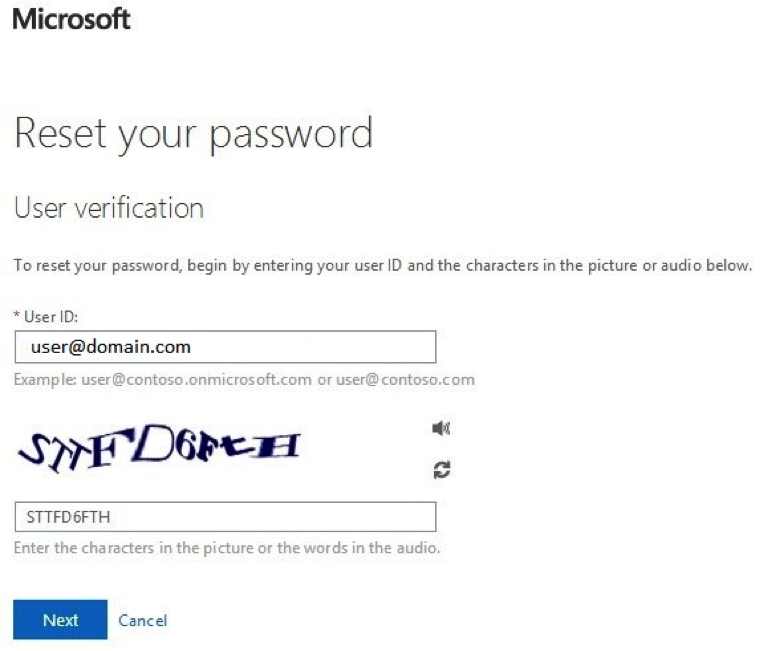
3. Since the user has specified an office phone, mobile phone, and alternate email in this case, you see that they have been given all of those as options to pass the first challenge.
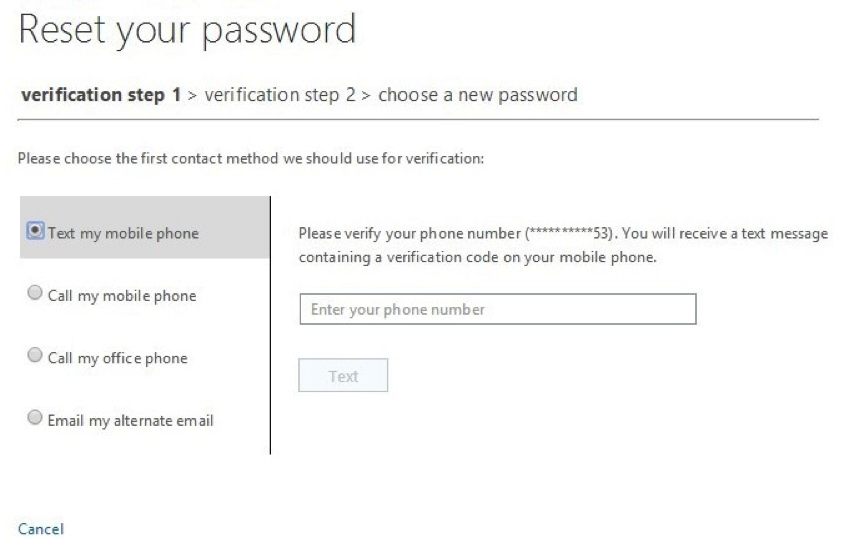
4. In this case, choose to call the office phone first. Note that when selecting a phone-based method, users will be asked to verify their phone number before they can reset their passwords. This is to prevent malicious use of phone numbers of users in your organization.
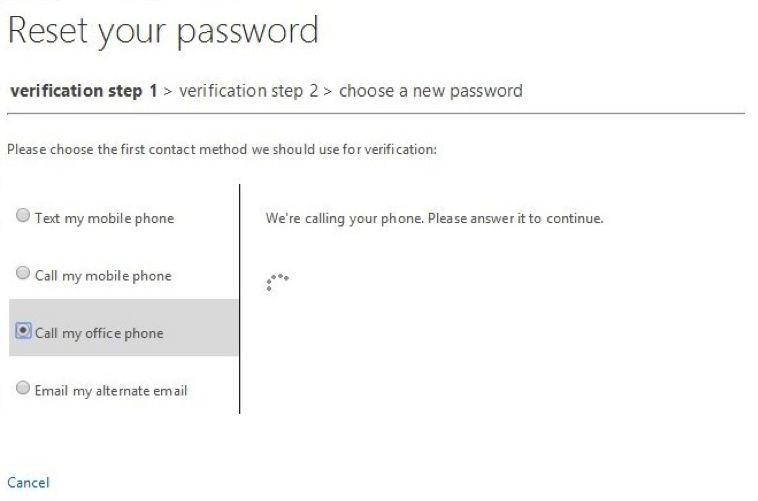
5. Once the user confirms their phone number, clicking “Call” will cause a spinner to appear and the phone will ring. A message will play once they answer the phone indicating that the user should press “#” to verify their account. Pressing this key will automatically verify that the user possesses the first challenge and advance the UI to the second verification step.
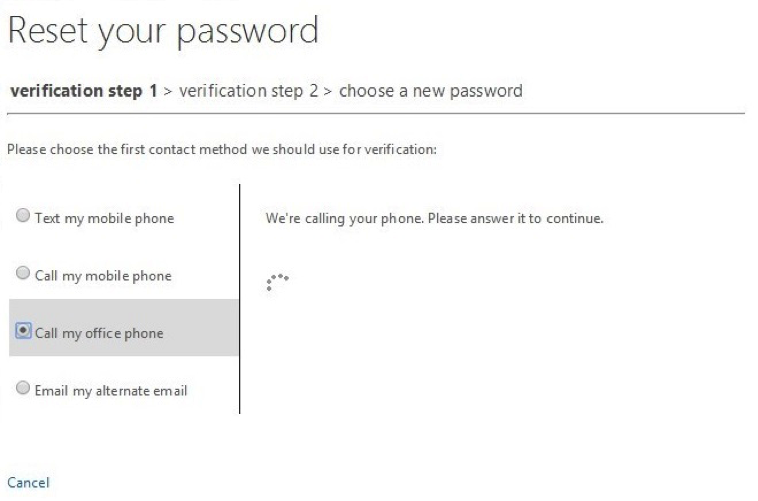
6. Once they’ve passed the first challenge, the UI is automatically updated to remove it from the list of choices the user has. In this case, because they used the office phone first, only mobile phone and alternate email remain as valid options to use as the challenge for the second verification step. In this case, pressing “Email” will email the alternate email on file.
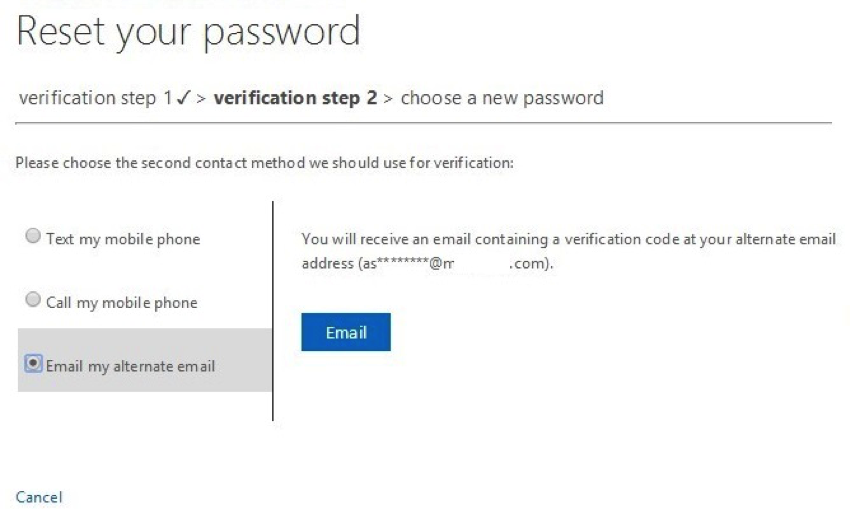
7. Here is the email users will see:
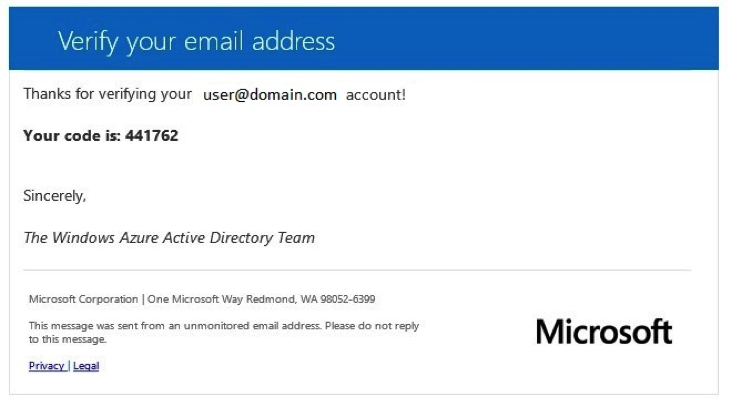
8. Once the email arrives, the page will update, and they will be able to enter the verification found in the email in the input box shown below. After a proper code is entered, the next button lights up, and they are able to pass through the second verification step.
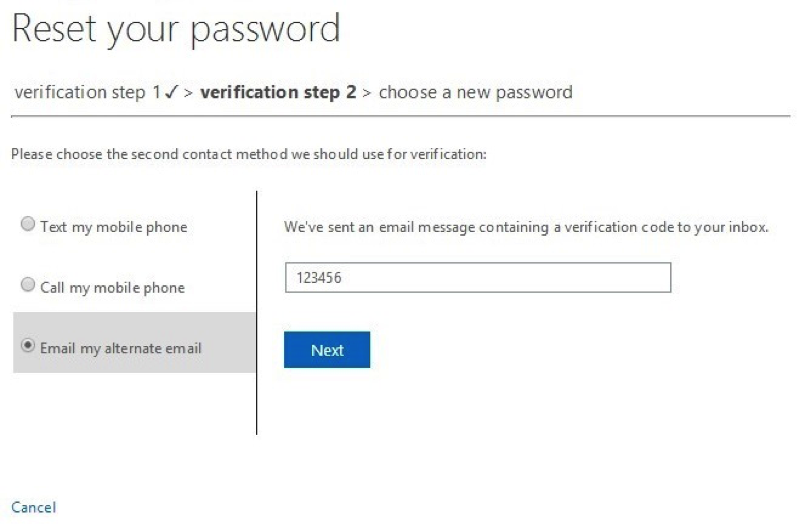
9. Once they have met the requirements of the organizational policy, they are allowed to choose a new password. The password is validated once it meets AD’s “strong” password requirements (password policy in Azure AD), and a strength validator appears to indicate to the user whether the password entered meets that policy.
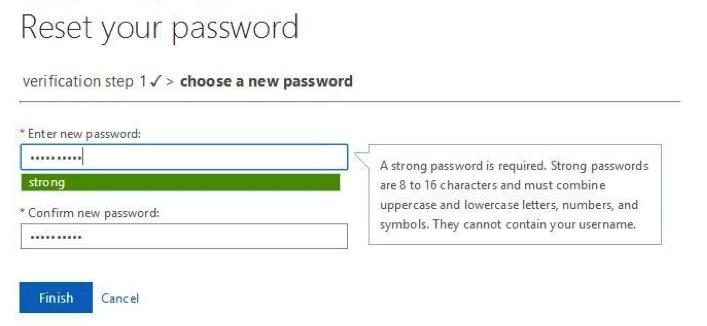
10. Once they provide matching passwords that meet your organizational policy, the password is reset and they can now log in with the new password.
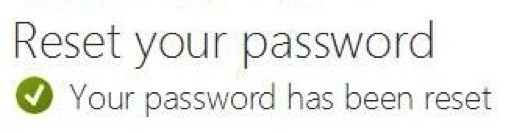
I know what you’re thinking, that was a lot of steps! Yes it very well may be, but bear in mind that IT administrators can control the number of verifications and our users, well they should feel empowered! Not only were they able to reset their own password, they didn’t even have to call the help desk. The trade-off? We normally see users call or email (from a non-work account) to have their passwords reset or unlocked. Our help desk then calls and verifies (at least we hope) some type of information with them and either emails them (on a non-work email) or texts them their new password! Not very secure, and not very efficient. Welcome to the new self-service password reset world!
Are you struggling with a password reset solution or user self-service and need additional information or real world expertise? Credera has extensive experience in acquiring, designing, planning, and implementing identity management systems that provide both cloud and on-premises capabilities. If you have questions about this blog post, points of view, or IT infrastructure, please use the comment section below or contact us on Twitter at @CrederaMSFT
Happy password resetting!
Contact Us
Let's talk!
We're ready to help turn your biggest challenges into your biggest advantages.
Searching for a new career?
View job openings


